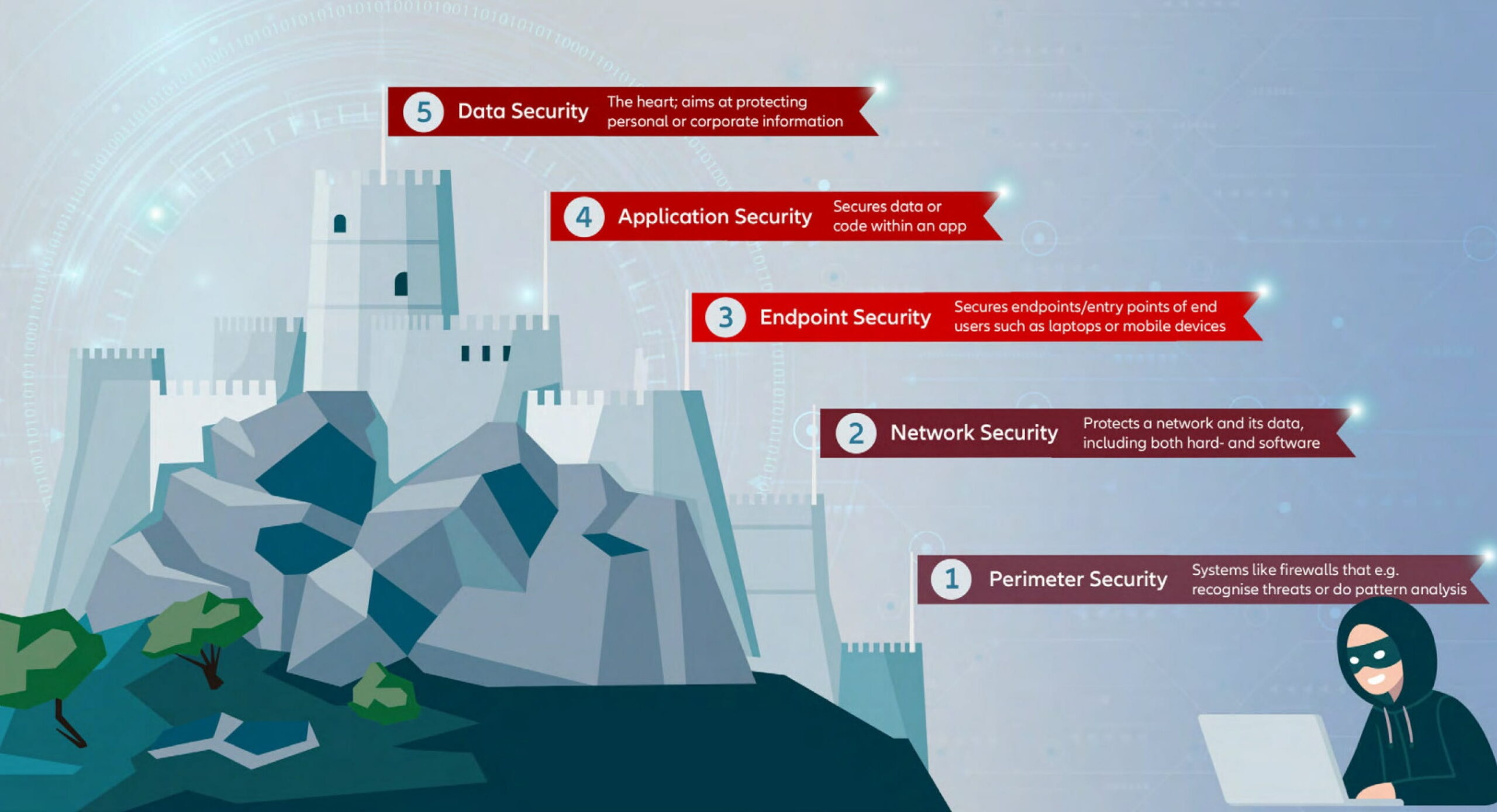
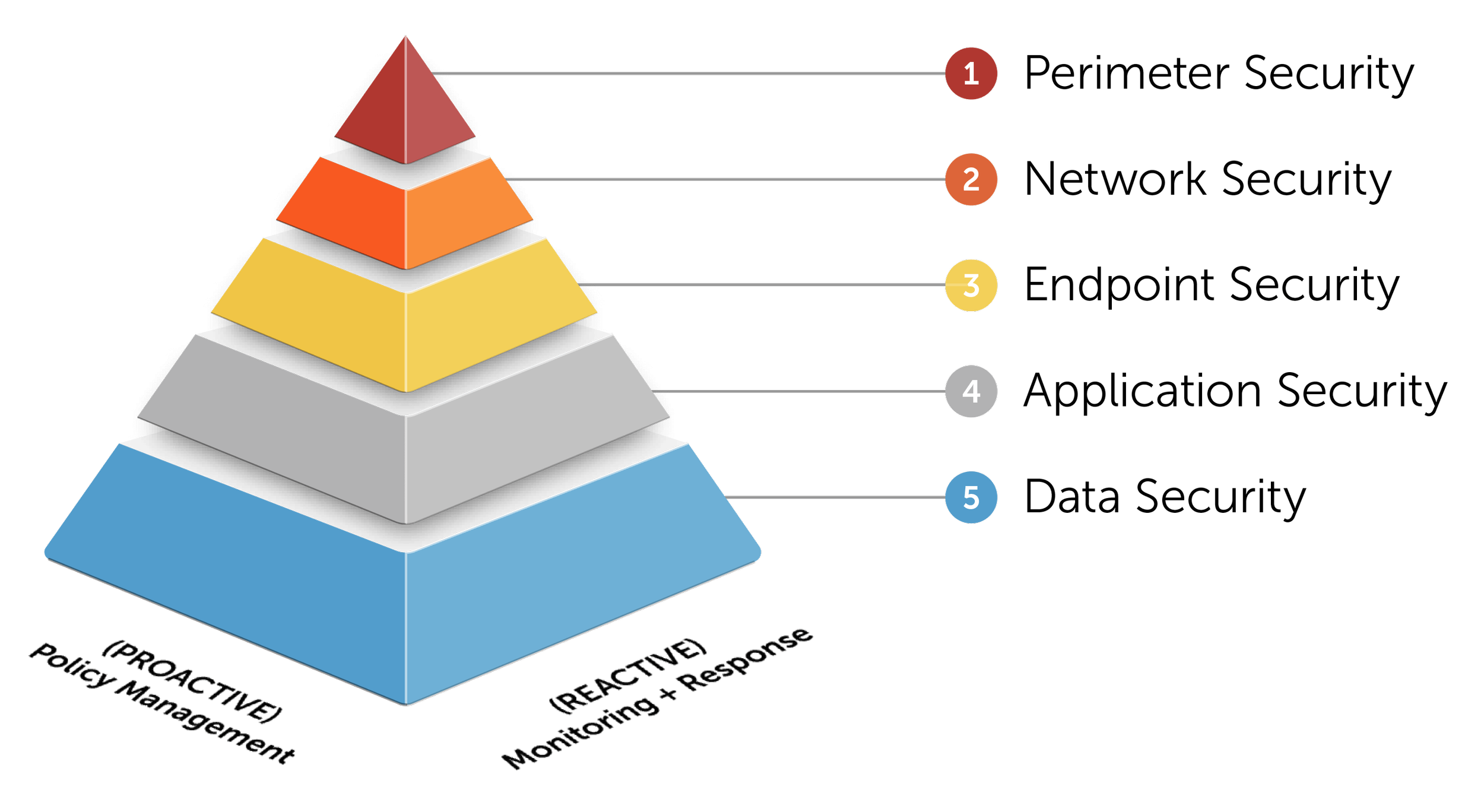
“Explore the five essential layers of cyber security that form a comprehensive defense strategy against cyber threats. Understand the importance of each layer, including network security, data protection, and incident response, to strengthen your overall security posture.”
In today’s digital landscape, securing sensitive information and systems from cyber threats is paramount. Understanding the five layers of cyber security provides a robust framework for safeguarding against potential attacks. Each layer plays a crucial role in forming a multi-faceted defense strategy. This comprehensive guide will explore these layers in detail, illustrating how they work together to create a resilient security posture.
1. Network Security Layers
Network Security is the foundation of cyber defense, focusing on protecting the integrity, confidentiality, and availability of data as it travels across or is accessed through network systems. This layer involves a combination of hardware and software solutions designed to shield networks from intrusions and other malicious activities.
Key Components:
- Firewalls: Act as barriers between trusted internal networks and untrusted external networks, blocking unauthorized access while allowing legitimate traffic.
- Intrusion Detection Systems (IDS): Monitor network traffic for suspicious activities and potential threats, alerting administrators of possible breaches.
- Virtual Private Networks (VPNs): Encrypt data transmitted over the internet, ensuring secure communication channels for remote users.
Example:
A financial institution might deploy a firewall to protect its internal network from external attacks while using an IDS to monitor for unusual activity indicative of a potential breach.
Statistic:
According to a 2023 report by Cybersecurity Ventures, global spending on network security solutions is projected to exceed $50 billion by 2026, highlighting the growing importance of this layer.
2. Data Protection Layers
Data Protection focuses on securing sensitive and critical information from unauthorized access, breaches, and corruption. This layer involves various practices and technologies designed to ensure data integrity and confidentiality.
Key Components:
- Encryption: Converts data into an unreadable format for unauthorized users, ensuring that only those with the decryption key can access the information.
- Data Masking: Hides sensitive information within a database so that it is not exposed during testing or processing activities.
- Backup Solutions: Regularly create copies of data to recover it in case of loss or corruption.
Example:
An e-commerce company may use encryption to protect customer credit card information during online transactions and implement regular backups to safeguard against data loss.
Quote:
“Data is a precious thing and will last longer than the systems themselves.” — Tim Berners-Lee
Statistic:
A 2024 survey by Veeam found that 78% of organizations experienced data loss in the past year, underscoring the critical need for effective data protection strategies.
3. Access Control Layers
Access Control ensures that only authorized individuals or systems can access specific resources or data. This layer involves managing permissions and implementing authentication mechanisms to verify the identity of users and devices.

Key Components:
- Authentication: The process of verifying the identity of a user or system, often through passwords, biometrics, or multi-factor authentication (MFA).
- Authorization: Determines the level of access granted to authenticated users, ensuring they can only access resources necessary for their role.
- Access Control Lists (ACLs): Define permissions for various users or groups, controlling what actions they can perform on specific resources.
Example:
A company may use MFA to ensure that only authorized employees can access its internal systems, requiring a password and a fingerprint scan to log in.
Statistic:
According to a 2024 report by Gartner, 90% of organizations that implemented MFA saw a significant reduction in security breaches, highlighting the effectiveness of this access control measure.
4. Incident Response Layers
Incident Response involves preparing for, detecting, and managing security incidents or breaches. This layer is crucial for minimizing the impact of an attack and recovering quickly from disruptions.
Key Components:
- Incident Response Plan: A predefined strategy detailing the steps to be taken in the event of a security incident, including communication protocols and recovery procedures.
- Forensic Analysis: Investigates the cause and impact of a security breach to understand how it occurred and to prevent future incidents.
- Response Teams: Specialized groups trained to handle security incidents, including IT staff, legal advisors, and communication experts.
Example:
When a data breach occurs, an organization might activate its incident response plan, mobilize its response team, and conduct a forensic analysis to determine the breach’s scope and impact.
Quote:
“Preparedness is the key to success in incident management. The faster you respond, the quicker you can minimize damage.” — Anonymous
Statistic:
A study by Ponemon Institute in 2023 revealed that organizations with a well-defined incident response plan experienced 40% lower costs related to data breaches compared to those without a plan.
5. Risk Management Layers
Risk Management involves identifying, assessing, and mitigating risks associated with cyber threats. This layer focuses on evaluating potential threats and vulnerabilities and implementing strategies to manage and reduce risk.
Key Components:
- Risk Assessment: The process of identifying potential threats and vulnerabilities, and evaluating their potential impact on the organization.
- Risk Mitigation: Implementing controls and measures to reduce the likelihood or impact of identified risks, such as deploying security technologies or adopting best practices.
- Compliance Management: Ensuring adherence to regulatory requirements and industry standards related to cyber security.
Example:
An organization might conduct a risk assessment to identify potential vulnerabilities in its systems, then implement security measures such as regular updates and patches to mitigate those risks.
Statistic:
A report by McKinsey & Company in 2023 found that companies with robust risk management practices experienced 50% fewer security incidents compared to those with less developed risk management strategies.

Conclusion
Understanding the five layers of cyber security — Network Security, Data Protection, Access Control, Incident Response, and Risk Management — is essential for building a comprehensive defense strategy against cyber threats. By implementing and integrating these layers, organizations can create a multi-faceted security framework that protects their assets and ensures a resilient security posture.
Each layer contributes to an overall security strategy that addresses various aspects of cyber defense, from protecting network infrastructure and sensitive data to managing risks and responding to incidents. Embracing these layers as part of a holistic security approach will help safeguard against evolving cyber threats and enhance the overall resilience of your security infrastructure.